Everything you need to know about the Hafnium exploit
What is the Hafnium exploit?
The Hafnium exploit is a Microsoft Exchange Server cyber attack and email hack, originally discovered in December 2020 but not made public until January 2021. It affected thousands of on-premise email customers, ranging from small businesses through to much larger enterprises and even governments worldwide. Microsoft was slow to react, only releasing a patch to address the problem in March 2021.
What effect does the Hafnium exploit have?
The effect of the exploit is to give hackers remote control of the victims’ systems. Microsoft confirmed that “the threat actor…accessed on premise Exchange servers which enabled access to email accounts, and allowed the installation of additional malware to facilitate long term access to victim environments.” The attackers exploit four zero day bugs in Microsoft Exchange Server, allowing them to steal victims’ data and perform numerous other malicious actions designed to further compromise their victims including potentially deploying ransomware to infected organisations.
Who is affected by the Hafnium exploit?
It seems that the prime targets of this exploit, certainly initially, were primarily organisations in the US in fields such as infectious disease research, education, defence, government, policy think tanks and the law. Indeed, the US Cybersecurity and Infrastructure Security Agency (CISA) was so concerned about Hafnium that it ordered all US government agencies to either install the Hafnium patch immediately or disconnect their on-premise exchange servers.
However, any organisation running an on-premise exchange server is potentially vulnerable to this exploit and there’s no indication that the threat is exclusive to the kinds of organisations listed above. Anyone can be affected, and the implications are potentially very serious so if you’re running an on-premise exchange server then you need to take action now if you have not done so already.
What impact has the Hafnium exploit had on Allware’s clients?
At Allware we look after a number of on-premise exchange servers and by the time we were alerted to the Hafnium exploit some of them had indeed been infected. After sifting through all the information that was coming out, the common infection points were the folders:
C:\program files\Microsoft\Exchange\ then the Client Access or the FrontEnd folder in here.
We had servers that had had their permissions changed on some or all of the sub folders in here which resulted in checking with known working servers to find out what the permissions should be. The main problem here was the removal of the “authenticated users” group from the HTTPProxy folder which needs to have read access, and to the sub folders. In addition to this we were finding so called web shells in some sub folders in here which thankfully could just be removed.
However, in the worst case of infection we discovered much more. On this server the C:\windows\help\help folder had a mimikatz.log file in which contained a complete list of every user account and password in the domain. We found processes running that we didn’t recognise, for example:
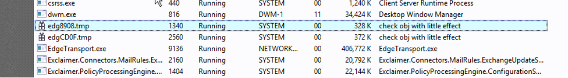
C:\windows\temp\Winword.exe was another surprise which had to be removed.
This was when we turned to the excellent MalwareBytes, which identified several more infected files
C:\windows\sqhost.exe
C:\windows\zsvc.exe
And surprisingly C:\Program files\…..FrontEndTransport.exe
Clearly the attackers were trying to name these files something that would look normal on a server designed to obfuscate their real purpose. If ever there was a reason to purchase MalwareBytes and pay them the £30/year, this is it.
What does this mean for Microsoft Exchange and Office365?
In all of this, one of the things that has surprised me the most is how easy it has been to exploit on premise Exchange servers, given how far into the Exchange lifecycle we now are. I first was introduced to Exchange 5 when I started working at News International Newspapers in 1997 and it worked – it worked really well. We had the whole business running on email for the first time ever. However, attackers were writing malicious code for these early versions of Exchange even then. Still, as long as email remains a critical service for most businesses it’s likely that on premise Exchange will remain so we need to be able to ensure that our clients can use it safely.
Whilst we sell a lot of Office365 services to customers, we still sell a lot of On Premise Exchange solutions as well. Office365 doesn’t include a backup solution and does not include spam filtering, AV, phishing protection and so on unless you purchase a very expensive Enterprise license. Because of that we’ve seen customers go from paying £5K every 5 years, to paying £7K a year just for email!
Given that, it’s immensely frustrating that the world of IT support seems intent on pushing everyone to Office365. These additional costs need to be justified, a balanced case must be presented to the leadership team so they get the full picture and can consider all the options enabling them make an informed decision. Too many companies are being pushed into making poorly informed decisions about their email, and that is the fault of the IT department or outsourced IT support company.
How Allware can help you
At Allware we pride ourselves on being technology-agnostic and offering solutions from the full range of products available. We will recommend whatever option we think best suits your needs – not the most expensive one or the one that pays us the biggest commission. Sometimes Office365 is the best option but not always, and we certainly don’t start out with the assumption that everyone should end up using Office 365 as so many other IT support providers seem to do. Talk to us today about your email needs or any other aspect of your IT to see how we can help you.